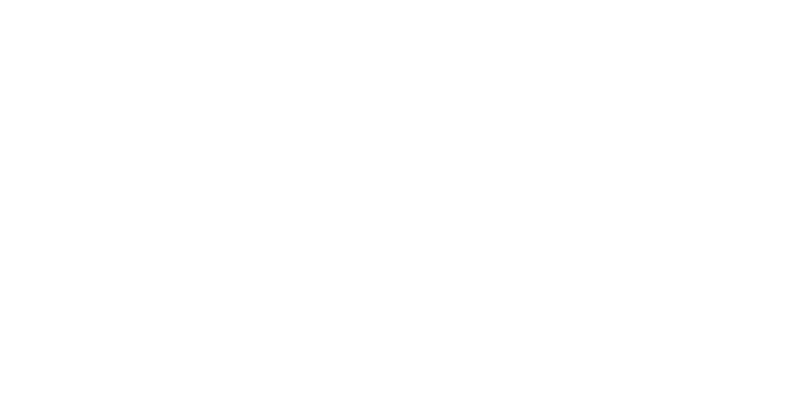
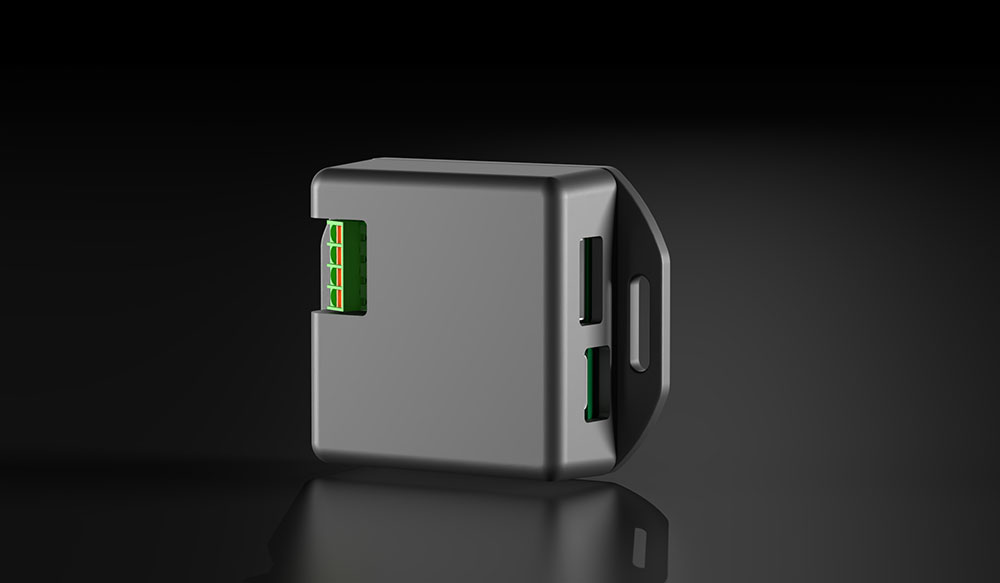
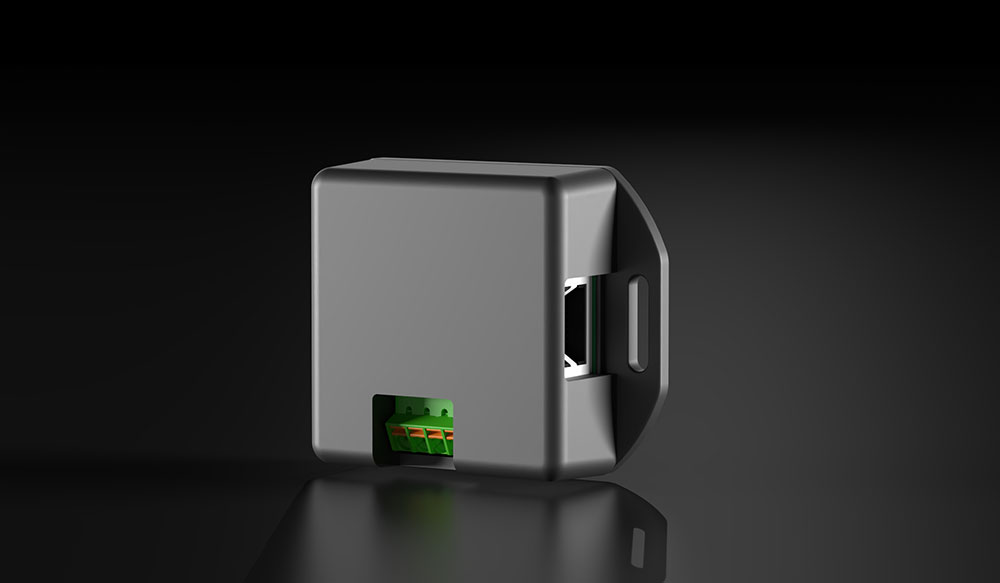
Increased security
Increased control of USB and Ethernet interfaces
Prevents unauthorised access and protects against cyber attacks
Interfaces are disabled by default, thus access is impossible
Only authorised personnel can activate the interface, for example via software (PLC/IPC, password protected) or key switch or RFID system connected in between

Simplicity
Easy integration into existing machines and plants
Compatibility
Compatible with CRA
Compatible with the Machinery Regulation 2027
Flexibility
Modular and flexible, adaptable to different application scenarios